 |
PS Hash v1.0
PS Hash v1.0
A program that calculates checksums and hashes of files, compares the contents of files using an algorithm specified by the user, verifying and generating checksum files (.md5, .sha1, .sha256 and others), calculating checksums of the given text.
PS Hash is a program that calculates checksums and hashes of files and given text.
The program supports 30 hashing algorithms, among others MD5, SHA-1, SHA-256, the SHA-3 algorithm family.
To facilitate the use of the program, the interface has been divided into thematic modules displayed on separate tabs.
File
The first module - File - allows you to calculate checksums of any files. The controls displaying the calculated values have been divided into groups and placed on collapsible panels. Each algorithm can be freely activated / deactivated, depending on the needs.
Files and folders can be added by drag and drop.
Log
The calculated checksums and hash functions values are automatically saved in the table in the second module - Log. This table allows you to view all previously calculated values, filter data based on specific criteria, sort, move rows and columns, delete unneeded data, as well as copy information to the clipboard and save to a text file.
To show or hide columns, right-click on the header of any column and in the context menu select the columns that are important to you and deselect those you do not need.
Compare
The third program module is used to compare the selected file with other files or a previously calculated checksum / hash.
Many software companies publish checksums of files made available for download from their servers. If you want to make sure that the downloaded file has not been modified in any way (during the download process or by malware), PS Hash allows you to easily check the originality of such a file by calculating the ... |
 |
3,548 |
May 09, 2020
Jacek Pazera 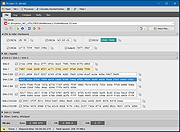 |
 |
Tom's Hash Explorer 1.2
Tom's Hash Explorer 1.2
Tom's Hash Explorer is a free Windows utility that allows you to easily calculate cryptographic hash values for single or multiple files in order to verify file integrity.
Tom's Hash Explorer features an innovative Explorer-like graphical user interface to navigate your file system and calculate cryptographic hash values for either a single file or for all files within a folder. The most popular Hash algorithms are supported, including MD5 Message-Digest Algorithm, SHA1 (160-bits), and SHA2 (256 bits, 384-bits, and 512 bits). Its multi-threaded hash computation engine results in extremely fast results.
Features
Innovative Explorer-like User Interface
Themes/Skins new.ping
Multi-Threaded Computation Engine
Calculate Hash Values using Industry Standard Hash Algorithms
Message Digest (MD5)
Secure Hashing Algorithm 1 (SHA-1)
Secure Hashing Algorithm 2 (SHA 256, SHA 384, SHA 512)
Calulate File Entropy using Shannon’s Entropy Algorithm new.ping
Calculate Hash Values or Entropy for Single File or Multiple Files
Drag and Drop new.ping
Save Hash Values to Text File or Copy to Clipboard for easy import into Whitelisting applications
Export Full Results
Microsoft Excel (XLS)
Comma Separated Values File (CSV)
Rich Text Format (RTF)
Adobe Acrobat Portable Document Format (PDF)
Print Full Results
Print Preview with Page Setup, Header & Footer, Watermark
“Tests show that the MD5 hash value is computed in ... |
 |
5,680 |
Aug 06, 2024
Tom Andreas Mannerud 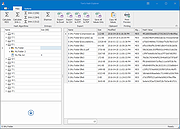 |














