 |
Recently Created or Modified Executables Search v2.1.0.2
Recently Created or Modified Executables Search v2.1.0.2
Free tool for incident response.
Inspect executable modules created or modified on your computer during a recent time window (cybersecurity incident time) you select. Returns each module's metadata along with the file's SHA-256 value. Helps discover file artifacts from malware incidents.
More info:
This application may be used at no cost after reading and accepting the built-in EULA. Write access to the Application's working directory is required for the product license file. Uniquely identify executable modules, file artifacts, deposited by System processes and unsafe user activity during a Cybersecurity incident time. Helps associate modules with unsafe or risky applications. Intended target audience: Cybersecurity, Network, Systems Analysts, and similar technical users.
SHA-256: 239fbc57cafdadeec735bf12aa1453b5c8858af16286c8606c8a7d2c7340bc22
Supported operating systems:
Windows 10/11 64bit
Important Notes:
1) This program will not function unless you install Microsoft .NET 6.0. Get it HERE.
2) This program will not function unless you right-click the file and choose to run as an administrator.
3) Once launched, allow the program to finish it's scan operation. This may take a few minutes.
|
 |
2,997 |
May 07, 2024
Steve Chaison Software 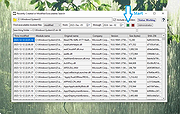 |














