 |
Block Attack - Rise of the Blocks v2.5.0
Block Attack - Rise of the Blocks v2.5.0
Block Attack - Rise of the Blocks is a puzzle/blockfall game inspired by Nintendo’s Tetris Attack for the Super Nintendo. The game is pretty action packed for a puzzle game :-) The game is programmed by me (Poul Sander) and is released under the GPL license version 2.
Features:
Based on the classic “Tetris Attack” for the SNES
5 single player modes: Endless, Time Trial, Puzzle Mode, Stage Clear and Vs. Mode
2 two player options: Time Trial and Vs. Mode
Puzzle mode has 30+ puzzles
Players can use a custom key setup
Handicap in (local)multi player
High scores are saved
Joypad support
Music and sound effects
Animations
Puzzle level editor (written in Java)
Select puzzle file from a list in the game
Runs under Linux and Windows + more
Save/Play Replay function
Network play, you must know the IP address of the server (uses enet)
Click here to visit the author's website. |
 |
5,855 |
Dec 08, 2019
Poul Sander  |
 |
F3D v2.5.0
F3D v2.5.0
Fast and minimalist 3D viewer
F3D (pronounced /fɛd/) is a fast and minimalist 3D viewer desktop application. It supports many file formats, from digital content to scientific datasets (including glTF, USD, STL, STEP, PLY, OBJ, FBX, Alembic), can show animations and support thumbnails and many rendering and texturing options including real time physically based rendering and raytracing.
It is fully controllable from the command line and support configuration files. It can provide thumbnails, support interactive hotkeys, drag&drop and integration into file managers.
F3D also contains the libf3d, a simple library to render meshes, with C++ and Python Bindings, as well as experimental Java and Javascript bindings.
User Documentation
https://f3d.app/doc/user/README_USER.html
Changes
v2.5.0
For F3D users:
Added a Webassembly version available online: https://f3d.app/web
Added a “neutral” tone mapping feature
Added an screenshot feature when pressing F12, with its dedicated option, --screenshot-filename
Added a --final-shader option to customize post-processing.
Added a --grid-color option to set the color of the grid
Added a --animation-progress option to control if the animation progress bar should be shown
Added a --backface-type option to control backface visibility
Added a concept of filename template for saving screenshots and outputs
Added native menus for macOS
Improved documentation all around
Reworked config file logic to avoid duplicating of the default config
Fixed a long standing issue with FBX skinning animation
Fixed zsh completion
Fixed an opacity blending issue
Fixed a crash when dropping a HDRI while playing an animation
Fixed a focus issue on macOS
Fixed a high DPI issue on Windows
For ... |
 |
732 |
Dec 26, 2024
Michael Migliore and Mathieu Westphal 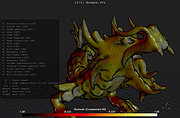 |
 |
Tweaking.com - Hardware Identify (PORTABLE) v2.5.0
Tweaking.com - Hardware Identify (PORTABLE) v2.5.0
Tweaking.com - Hardware Identify will help identify unknown hardware on your system. This program does not help you download drivers but helps let you know what the hardware is, so you know what drivers to find.
For example, say you just reinstalled a computer and the device manager shows multiple unknown hardware with no drivers installed. Well, you don't know what drivers to find since you don't know what the hardware is. Now with Tweaking.com - Hardware Identify you can see what that hardware is.
The program also has an easy option to help improve the device database. Once you have all drivers installed, you can have the program check for any hardware on the system that isn't in the database and submit it to Tweaking.com. Within a few days, the database will be updated, and the device list will grow with the help of users like you!
Changes:
v2.5.0
Major changes to the graphics and controls of the program. Now supports high DPI systems and has improved graphics.
Multiple bug fixes and improvements.
Click here to visit the author's website. |
 |
8,718 |
Jul 02, 2019
Tweaking.com 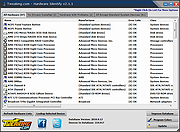 |
 |
Wifinian v2.5.0
Wifinian v2.5.0
More control over Wi-Fi connections!
Wifinian is a Windows desktop tool to enable user to actively control Wi-Fi connections.
Functions:
Connect to or disconnect from a wireless network
Rename a wireless profile
Change automatic connection (Auto Connect) or automatic switch (Auto Switch) settings of a wireless profile
Rush - Perform rescan of wireless networks in short intervals (The number indicates interval (sec).)
Engage - Execute automatic connection depending on signal strength, order and automatic switch setting of wireless profiles (The number indicates threshold of signal strength (%).)
Organize - Change the order (priority) of wireless profiles, delete a wireless profile
Requirements
Windows 7 or newer
.NET Framework 4.8
Remarks
To rename a wireless profile, press and hold its name.
Rescan of wireless networks by OS itself is triggered by some actions and if no such actions take place, seems to be performed once per one minute.
Automatic connection by Engage function applies only to wireless profiles whose automatic switch are enabled. If a profile whose automatic switch is not enabled has been already connected, automatic connection will not be executed.
When you connect to a wireless network by OS's wireless menu, the order of wireless profiles may be automatically changed.
A wireless profile is associated with a specific wireless adapter and if the adapter is not in place, such profile will not be shown.
License
MIT License
How to delete wireless profiles from OS's GUI
The GUI to delete wireless profiles has come back in Windows 8.1 Update. To reach this GUI, see the following.
Windows 10
[Network settings] from notification area (or [Settings] from ... |
 |
3,030 |
Dec 22, 2020
emoacht 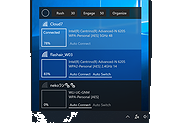 |
 |
WindTerm v2.5.0
WindTerm v2.5.0
A Quicker and better SSH/Telnet/Serial/Shell/Sftp client for DevOps.
License
Completely FREE for commercial and non-commercial use without limitations. All released source codes (except thirdparty directory) are provided under the terms of Apache-2.0 license.
Introduction
See Intro Videos
https://kingtoolbox.github.io/
Screenshots
Main Window (zsh):
Split views:
DigeWhite Theme:
Features
SSH, Telnet, Tcp, Shell, Serial
SSH v2, Telnet, Raw Tcp, Serial, Shell protocols implemented.
Supports SSH auto execution when session authenticated.
Supports SSH ControlMaster.
Supports SSH ProxyCommand or ProxyJump.
Supports SSH agent forwarding.
Supports SSH auto login with password, public-key, keyboard-interactive, gssapi-with-mic.
Supports X11 forwarding.
Supports direct/local port forwarding, reverse/remote port forwarding and dynamic port forwarding.
Supports XModem, YModem and ZModem.
Integrated sftp, scp client, supports download, upload, remove, rename, make new file/directory and so on.
Integrated local file manager, supports move to, copy to, copy from, remove, rename, make new file/directory and so on.
Supports Windows Cmd, PowerShell and Cmd, PowerShell as administrator.
Supports Linux bash, zsh, powershell core and so on.
Supports MacOS bash, zsh, powershell core and so on.
GUI
Supports Windows, MacOS and Linux.
Supports Multilingual User Interface.
Supports Unicode 13.
Session dialog and session tree.
Free Type Mode.
Focus Mode.
Sync Input.
Enhanced protection of the session username and password.
Command palette.
Command sender.
Explorer Pane.
Shell Pane.
Quick Bar.
... |
 |
2,185 |
May 24, 2023
kingToolbox 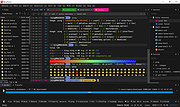 |

















