 |
Bitdefender Home Scanner 1.0
Bitdefender Home Scanner 1.0
Scan for weaknesses and hidden backdoors into your home
Bitdefender Home Scanner is a free tool that scans your Wi-Fi network, maps devices and identifies and highlights network security flaws. Bitdefender Home Scanner looks for weak passwords, as well as vulnerable or poorly encrypted communications. It correlates the information gathered from your connected devices with online vulnerability databases and gives you a thorough report so you can ensure maximum security for your network.
Map your home network
Scan open ports in the network
Wi-Fi scanner: identify all connected devices and security risks
Complementary to and compatible with all existing security tools
Why use Bitdefender Home Scanner
New software vulnerabilities are being discovered in many smart devices every day, and hackers are taking advantage of these security flaws to target homes and businesses. It is time to start thinking about the security of your smart devices.
Recently, a mom who had installed a smart surveillance system in her home discovered that someone had hacked into a webcam and live-streamed her daughters’ room on the Internet.
There have been numerous reports about light bulbs being hacked. In one case, a security company demonstrated that unauthorized persons could hack into a home network by posing as a new light bulb joining the system. This way the other light bulbs were tricked into giving away the username and password for the network.
Moreover, hackers can take advantage of vulnerabilities to take control of vast numbers of smart devices and use them to launch massive attacks against commercial and government websites.
Technical Details
Minimum system requirements:
Windows 7 SP 1, 8, 8.1, 10
CPU: Dual Core 1.6 GHz
RAM: 1 GB
HDD: 300 MB
Recommended system requirements:
Windows 7 SP ... |
 |
5,364 |
Nov 13, 2019
BitDefender Labs 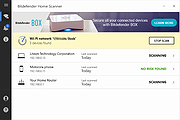 |
 |
BruteShark v1.2.5
BruteShark v1.2.5
A Network Forensic Analysis Tool (NFAT) that performs deep processing and inspection of network traffic (mainly PCAP files).
It includes: password extracting, building a network map, reconstruct TCP sessions, extract hashes of encrypted passwords and even convert them to a Hashcat format in order to perform an offline Brute Force attack.
The main goal of the project is to provide solution to security researchers and network administrators with the task of network traffic analysis while they try to identify weaknesses that can be used by a potential attacker to gain access to critical points on the network.
Two BruteShark versions are available, A GUI based application (Windows) and a Command Line Interface tool (Windows and Linux).
The various projects in the solution can also be used independently as infrastructure for analyzing network traffic on Linux or Windows machines. For further details see the Architecture section.
What it can do
Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
Build visual network diagram (Network nodes & users)
Reconstruct all TCP & UDP Sessions
File Carving
Windows Prerequisites:
WinPcap / Npcap driver (Wireshark installs one of this by default)
.NET Core SDK
Linux Prerequisites:
libpcap driver
Examples
Videos
Hashes Extracting
Building a Network Diagram
File Carving
Password Extracting
Reconstruct all TCP Sessions
Brute Shark CLI
Architecture
All BruteShark projects are implemented using .Net Core and .Net Standard for modern and cross platform support. The solution is designed with three layer architecture, including a one or more projects at each layer - DAL, BLL and PL. The separation between layers is created by the fact that each project refers only its own objects.
PcapProcessor (DAL)
As ... |
 |
3,434 |
Jun 13, 2023
Oded Shimon 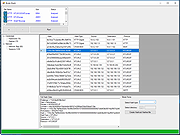 |
 |
CyberChef v10.4.0
CyberChef v10.4.0
The Cyber Swiss Army Knife by the UK Government Code and Cypher School (GCHQ)
CyberChef is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
The tool is designed to enable both technical and non-technical analysts to manipulate data in complex ways without having to deal with complex tools or algorithms. It was conceived, designed, built and incrementally improved by an analyst in their 10% innovation time over several years.
Live demo
• CyberChef is still under active development. As a result, it shouldn't be considered a finished product. There is still testing and bug fixing to do, new features to be added and additional documentation to write. Please contribute!
• Cryptographic operations in CyberChef should not be relied upon to provide security in any situation. No guarantee is offered for their correctness.
• A live demo can be found here - have fun!
How it works
There are four main areas in CyberChef:
1) The input box in the top right, where you can paste, type or drag the text or file you want to operate on.
2) The output box in the bottom right, where the outcome of your processing will be displayed.
3) The operations list on the far left, where you can find all the operations that CyberChef is capable of in categorised lists, or by searching.
4) The recipe area in the middle, where you can drag the operations ... |
 |
3,474 |
May 24, 2023
UK's Government Code and Cypher School 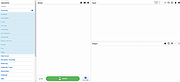 |
 |
EOPRadar v1.08
EOPRadar v1.08
Use this new tool to check your system for several classes of privilege escalation vulnerabilities.
Useful in pentesting engagements, OS image hardening, SRP/AppLocker testing.
Win 7 and above. x64 only
Quick start
1. Note that the tool must be launched as a standard user account (SUA) - not an administrator.
2. Launch the application and click Scan.
3. In the scan results, a warning (yellow) indicates a writable process path, while an alert (red) indicates a critical EOP vulnerability, which would allow any standard user to elevate privileges to administrator. Any findings in red should be taken very seriously, especially in a AD domain environment.
4. Based on the results, review and fix your NTFS permissions for the affected processes. Remember, SUA-writable paths should not be executable, and vice versa.
Click here to visit the author's website. |
 |
4,838 |
Dec 18, 2019
FS1 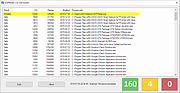 |
 |
ESET EternalBlue Checker 1.0.0.1
ESET EternalBlue Checker 1.0.0.1
ESET has released a free tool to help determine whether your Windows machine is patched against EternalBlue.
If the tool finds a vulnerability in your system due to missing Microsoft patches, Your computer is vulnerable will be displayed.
Press any key to open the Microsoft Windows update page. Click Microsoft Update Catalog in Method 2: Microsoft update Catalog section.
On the Microsoft Update Catalog page, find your operating system in the Products column and click the Download button next to your system.
Click the link in the Download window to download the security update for your system.
After the security update has been installed, restart your computer.
After the computer has restarted, run ESETEternalBlueChecker.exe again to verify that the security update installed correctly and your system is no longer at risk. If the security update was installed correctly, Your computer is safe, Microsoft security update is already installed will be displayed.
Warn colleagues who frequently receive emails from external sources – for instance financial departments or Human Resources.
Regularly back up your data. In the event of infection, this will help you recover all data. Do not leave external storage used for backups connected to your computer to eliminate the risk of infecting your backups. If your system requires Windows Updates to receive the patch for this exploit, create new backups after applying the patch.
Disable or restrict Remote Desktop Protocol (RDP) access
Disable macros in Microsoft Office.
If you are using Windows XP, disable SMBv1. |
 |
5,391 |
Nov 13, 2019
ESET 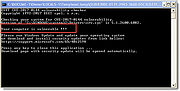 |
 |
Eternal Blues 0.0.0.8
Eternal Blues 0.0.0.8
Eternal Blues is a free EternalBlue vulnerability scanner. It helps finding the blind spots in your network, these endpoints that are still vulnerable to EternalBlue.
Just hit the SCAN button and you will immediately start to get which of your computers are vulnerable and which aren’t. That’s it.
If you wish, you can switch networks, or edit your own (yeah, you can also scan the world wide web if you wish). Please use it for good cause only. We have enough bad guys already…
Was this tool tested in real networks?
Oh yeah. Obviously I cannot say which, but with almost every network I connected to, there were a few vulnerable computers.
IMPORTANT: It does *not* exploit the vulnerability, but just checks whether it is exploitable.
Yet another vulnerability scanner?
There are many vulnerability scanners out there. So… why did I create another? Mainly for the ease of use. The majority of latest WannaCry, NoPetya (Petya, GoldenEye or whatever) victims, are not technical organizations and sometimes just small business who don’t have a security team, or even just an IT team to help them mitigate this. Running NMap, Metasploit (not to mention more commercial products) is something they will never do. I aimed to create a simple ‘one-button’ tool that tells you one thing and one thing only – which systems are vulnerable in your network.
Tips
If you’re about to run it in your working environment, please update the IT/Security team in advance. You don’t want to cause (IDS/IPS/AV) false alarms
If vulnerable systems were found – please take a Windows update asap
For God’s sake, please disable SMBv1 already. Whether your systems are patched or not. This protocol was written over 3 decades ago…!
If you would like to enjoy the ... |
 |
5,332 |
Nov 13, 2019
Omerez 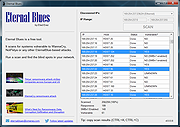 |
 |
GIGABYTE Intel ME Critical FW Update Utility vB18.0125.1
GIGABYTE Intel ME Critical FW Update Utility vB18.0125.1
GIGABYTE TECHNOLOGY Co. Ltd, a leading manufacturer of motherboards and graphics cards, has implemented safety measures aligned with Intel®’s response to the Intel Management Engine (ME) and Intel Trusted Execution Engine (TXE) security vulnerabilities, so customers can be reassured their motherboards are fully protected. For all customers who have purchased GIGABYTE motherboards for Intel platforms, please visit the official website to download the latest BIOS versions as well as ME and TXE drivers.
The updates for the motherboards will be released starting with the Z370, 200 and 100 series and then previous generation motherboards. GIGABYTE has released a safety update for the user’s convenience. The GIGABYTE Intel ME Critical FW Update Utility on the GIGABYTE website will automatically detect the system's ME version and update it to the latest version.
|
 |
5,418 |
Nov 13, 2019
Gigabyte  |
 |
Gophish v0.11.0
Gophish v0.11.0
Open-Source Phishing Framework.
Gophish is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing.
Launch a Campaign in 3 steps:
Set Templates & Targets
Gophish makes it easy to create or import pixel-perfect phishing templates.
Our web UI includes a full HTML editor, making it easy to customize your templates right in your browser.
Launch the Campaign
Launch the campaign and phishing emails are sent in the background. You can also schedule campaigns to launch whenever you'd like.
Track Results
Detailed results are delivered in near real-time. Results can be exported for use in reports.
View full installation and usage instructions here.
This download is for the Windows version.
If you need the MacOS version, download here.
If you need the Linux version, download here.
Click here to visit the author's website. |
 |
3,706 |
Oct 25, 2021
Jordan Wright  |
 |
Hardentools v2.1
Hardentools v2.1
A collection of simple utilities designed to disable a number of "features" exposed by operating systems (Microsoft Windows, for now), and primary consumer applications.
These features, commonly thought for enterprise customers, are generally useless to regular users and rather pose as dangers as they are very commonly abused by attackers to execute malicious code on a victim's computer. The intent of this tool is to simply reduce the attack surface by disabling the low-hanging fruit. Hardentools is intended for individuals at risk, who might want an extra level of security at the price of some usability. It is not intended for corporate environments.
WARNING: This tool disables a number of features, including of Microsoft Office, Adobe Reader, and Windows, that might cause malfunctions to certain applications. Use this at your own risk.
Disabled Features
Generic Windows Features
Disable Windows Script Host. Windows Script Host allows the execution of VBScript and JavaScript files on Windows operating systems. This is very commonly used by regular malware (such as ransomware) as well as targeted malware.
Disabling AutoRun and AutoPlay. Disables AutoRun / AutoPlay for all devices. This prevents applications from automatically executing when you plug a USB stick into your computer.
Disables powershell.exe and powershell_ise.exe execution via Windows Explorer. This prevents the use of PowerShell by malicious code trying to infect the system. You will not be able to open PowerShell directly anymore.
Disables cmd.exe execution via Windows Explorer (optional). You will not be able to use the cmd terminal and it should prevent malicious code trying to infect the system by using cmd.exe to e.g. start powershell.exe. This setting is optional because cmd.exe is used quite often by users and applications. This must therefore be enabled ... |
 |
4,655 |
Dec 05, 2021
Security Without Borders 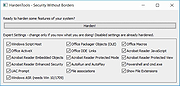 |
 |
InSpectre v8
InSpectre v8
Easily examine and understand any Windows
system's hardware and software capability to
prevent Meltdown and Spectre attacks.
“InSpectre” is an easy to use & understand utility designed to clarify
the many overlapping and confusing aspects of any Windows
system's ability to prevent the Meltdown and Spectre attacks.
As the application's textual display says...
In early 2018 the PC industry was rocked by the revelation that common processor design features, widely used to increase the performance of modern PCs, could be abused to create critical security vulnerabilities. The industry quickly responded, and is responding, to these Meltdown and Spectre threats by updating operating systems, motherboard BIOSes and CPU firmware.
Protection from these two significant vulnerabilities requires updates to every system's hardware–its BIOS which reloads updated processor firmware–and its operating system–to use the new processor features. To further complicate matters, newer processors contain features to minimize the performance impact of these important security improvements. But older processors, lacking these newer features, will be significantly burdened and system performance will suffer under some workloads.
This InSpectre utility was designed to clarify every system's current situation so that appropriate measures can be taken to update the system's hardware and software for maximum security and performance.
Release History
Release #8 — Now shows whether an Intel microcode patch is (ever) available for Spectre.
Intel has finished designing microcode update patches for its processors. On April 2nd, 2018, they announced that processors that have not yet been patches will never be patched. Their full statement is available in this PDF document. In that document, Intel specifies which of their many processors do have patches and which of their more recent processors will never receive updated firmware. Now that the industry has this information, this 8th release of InSpectre incorporates that list of CPUIDs and displays whether microcode firmware updates exist for the system's Intel CPU.
BOGUS “SmartScreen” ... |
 |
5,388 |
Nov 13, 2019
Gibson Research Corporation 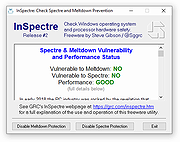 |
 |
log4j-scan v1.0
log4j-scan v1.0
A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228 on hosts.
Features
Support for lists of URLs.
Fuzzing for more than 60 HTTP request headers (not only 3-4 headers as previously seen tools).
Fuzzing for HTTP POST Data parameters.
Fuzzing for JSON data parameters.
Supports DNS callback for vulnerability discovery and validation.
WAF Bypass payloads.
Description
From the authors:
We have been researching the Log4J RCE (CVE-2021-44228) since it was released, and we worked in preventing this vulnerability with our customers. We are open-sourcing an open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability. This shall be used by security teams to scan their infrastructure for Log4J RCE, and also test for WAF bypasses that can result in achiving code execution on the organization's environment.
It supports DNS OOB callbacks out of the box, there is no need to setup a DNS callback server.
Usage
$ python3 log4j-scan.py -h
[•] CVE-2021-44228 - Apache Log4j RCE Scanner
[•] Scanner provided by FullHunt.io - The Next-Gen Attack Surface Management Platform.
[•] Secure your External Attack Surface with FullHunt.io.
usage: log4j-scan.py [-h] [-u URL] [-l USEDLIST] [--request-type REQUEST_TYPE] [--headers-file HEADERS_FILE] [--run-all-tests] [--exclude-user-agent-fuzzing]
[--wait-time WAIT_TIME] [--waf-bypass] [--dns-callback-provider DNS_CALLBACK_PROVIDER] [--custom-dns-callback-host CUSTOM_DNS_CALLBACK_HOST]
optional arguments:
-h, --help show this help message and exit
-u URL, --url URL Check a single URL.
-p PROXY, --proxy PROXY
Send requests through proxy.
... |
 |
2,327 |
Dec 15, 2021
Mazin Ahmed  |
 |
Malwarebytes Anti-Exploit v1.13.1.585
Malwarebytes Anti-Exploit v1.13.1.585
Protects you against the security vulnerabilities in the code, which make up your software programs. Your software contains millions of lines of code, which unfortunately some people want to exploit.
Malwarebytes Anti-Exploit protects you from these vulnerabilities which people can manipulate in order to infect your system with malware. The software gives you three layers of security protection around popular browsers and applications, thereby preventing the vulnerable code from being exploited.
The software is not an antivirus product in itself, but it is compatible with most antivirus software.
Features
• It protects browsers and their add-ons
• Protects browser components
• Protects media players and PDF readers
• Allows you to manage custom shields
• Best of all, it's free!
Changes:
v1.13.1.585
Stability/issues fixed:
Fixed issues with Chrome browser
Fixed false positives with MS Office products
Improved Logging capabilities
Internal Product Improvements
Click here to visit the author's website. |
 |
9,889 |
Apr 03, 2024
Malwarebytes 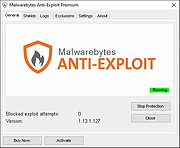 |
 |
Metasploitable v2.0.0
Metasploitable v2.0.0
This is Metasploitable2 (Linux)
Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools, and practice common penetration testing techniques.
The default login and password is msfadmin:msfadmin.
Never expose this VM to an untrusted network (use NAT or Host-only mode if you have any questions what that means).
Metasploitable 2 Exploitability Guide is HERE.
Click here to visit the author's website. |
 |
4,079 |
Nov 13, 2019
rapid7user  |
 |
Network Security Toolkit (NST) v38
Network Security Toolkit (NST) v38
A network security analysis and monitoring toolkit Linux distribution.
Network Security Toolkit (NST) is a bootable ISO image (Live USB Flash Drive) based on Fedora 36 providing easy access to best-of-breed Open Source Network Security Applications and should run on most x86_64 systems.
The main intent of developing this toolkit was to provide the security professional and network administrator with a comprehensive set of Open Source Network Security Tools. The majority of tools published in the article: Top 125 Security Tools by INSECURE.ORG are available in the toolkit. An advanced Web User Interface (WUI) is provided for system/network administration, navigation, automation, network monitoring, host geolocation, network analysis and configuration of many network and security applications found within the NST distribution. In the virtual world, NST can be used as a network security analysis, validation and monitoring tool on enterprise virtual servers hosting virtual machines.
Features
Multi-Tap Network Packet Capture
Web-Based Network Security Tools Management
Host/IPv4 Address Geolocation
Network/System Monitoring
Network Intrusion Detection
Network Interface Bandwidth Monitor
Web-based Snort IDS Integration
Active Connections Monitor
Network Segment ARP Scanner
Network Packet Capture CloudShark Upload Support
Multi-Port Terminal Server
VNC / RDP Desktop Session Management
Click here to visit the author's website. |
 |
2,962 |
Oct 03, 2023
networksecuritytoolkit.org 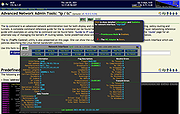 |
 |
Universal Radio Hacker v2.9.1
Universal Radio Hacker v2.9.1
The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios. URH allows easy demodulation of signals combined with an automatic detection of modulation parameters making it a breeze to identify the bits and bytes that fly over the air. As data often gets encoded before transmission, URH offers customizable decodings to crack even sophisticated encodings like CC1101 data whitening. When it comes to protocol reverse-engineering, URH is helpful in two ways. You can either manually assign protocol fields and message types or let URH automatically infer protocol fields with a rule-based intelligence. Finally, URH entails a fuzzing component aimed at stateless protocols and a simulation environment for stateful attacks.
Download user guide here.
Instructional Video:
This download is for the Windows 64bit version.
If you need the Windows 32bit version, download here.
If you need the MacOS version, download here.
If you need the Linux version, download here.
Changes:
v2.9.1
Dec 30, 2020
0c8f383 use *.wav format for demodulated signal export
8af7da3 change separation colors to green and magenta
a3eceba fix disappearing separation area in demod view
6a7048c fix #829
7d2e41b fix overflow in AutoInterpretation for certain signals
Click here to visit the author's website. |
 |
5,296 |
Feb 11, 2021
Dr. Johannes Pohl  |
 |
Waircut v2.0
Waircut v2.0
WPS wireless protocol audit software for Windows.
Wireless Air Cut is a WPS wireless, portable and free network audit software for Ms Windows.
It is used to check the security of our wps wireless networks and to detect possible security breaches.
You can check if the router has a generic and known wps pin set, if it is vulnerable to a brute-force attack or is vulnerable to a Pixie-Dust attack.
Features
Compatible with windows 7, 8, 8.1 and 10
Scans wireless networks with the WPS protocol enabled.
Compatible with pins that do not meet the checksum rule.
Several WPS pin generation algorithms: ZAO, Arcadyan LiveBox 2.1 / 2.2, FTE ...
Able to audit a pixie-dust attack on windows.
Editable and upgradable database of generic pins.
Multilingual, English, Spanish, French and Russian.
INSTALLATION:
This is a portable application so you only need to unzip it to a folder and run the file waircut.exe.
However, in order for the application to work, you must first install the JumpStart wireless network management software. If you already have it installed at other times you do not have to install it again. Another requirement is that you have installed the Microsoft .NET Framework 4.0.
You can download these dependencies from the following links:
Microsoft .net framework 4.0
Atheros jumpstart for wireless Drivers
Changes:
[2.0] - 2018-05-15 ### Fixed - Bug in WPS data base pin editor with empty SSID. - Function reimplementation for check new versión.
Click here to visit the author's website. |
 |
14,015 |
Nov 13, 2019
patcherr  |
 |
Win10 Security Plus v1.0
Win10 Security Plus v1.0
Win10 Security Plus is a powerful Windows OS software application that improves the security of Windows. It applies many recommended security settings and advanced security enhancements to the operating system, the changes should not cause conflicts or system errors, we have tested them many times. The program enables important security services, disables vulnerable system features (such as autorun.inf autoplay, NTVDM executions, Windows host script), improves the security of Internet Explorer and of the system integrity. And best of all, you just need to click the button "Apply Selected" and reboot the PC, that's all. This program works on Windows XP, Vista, 7, 8, 8.1, 10 (32\64-bit).
If you have programs that use cscript.exe or wscript.exe you should uncheck the option "Disable Windows Script Host". Else you may get an error message like "Windows Script Host access is disabled on this machine. Contact your administrator for details." when a program executes VBScript or JScript scripts.
Program Key Features
Enable Important System Security Services
Disable Commonly Exploited System Features
Disable Autorun.inf Autoplay, 16-bit Processes, WSCRIPT.EXE
Enable SmartScreen, Windows Updates, Windows Defender
Enable User Acces Control (UAC), Windows File Protection (SFC)
Activate Internet Explorer Memory Protection
Enable Structured Exception Handling Overwrite Protection
Disable Remote Registry, Remote Assistance, Short File Names
Enable Driver Signing Check, System Restore, Security Center
Enable Signature Verification of Downloaded Programs
40+ Security Improvements in One Powerful Program
Improves System Protection Against Malware
... |
 |
5,387 |
Nov 13, 2019
site2unblock 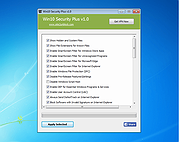 |





























