A Plea.
Deanna and I (Your Older Geeks) have been running OlderGeeks.com since 2008 and lately we are seeing a major increase in usage (and cost) but a big decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in.
Please donate on the website today. Every little bit helps.
Thank you so much.
-D&R
Always scroll to the bottom of the page for the main download link.
We don't believe in fake/misleading download buttons and tricks. The link is always in the same place.
Hardentools v2.1
A collection of simple utilities designed to disable a number of "features" exposed by operating systems (Microsoft Windows, for now), and primary consumer applications.
These features, commonly thought for enterprise customers, are generally useless to regular users and rather pose as dangers as they are very commonly abused by attackers to execute malicious code on a victim's computer. The intent of this tool is to simply reduce the attack surface by disabling the low-hanging fruit. Hardentools is intended for individuals at risk, who might want an extra level of security at the price of some usability. It is not intended for corporate environments.
WARNING: This tool disables a number of features, including of Microsoft Office, Adobe Reader, and Windows, that might cause malfunctions to certain applications. Use this at your own risk.
Disabled Features
Generic Windows Features
Disable Windows Script Host. Windows Script Host allows the execution of VBScript and JavaScript files on Windows operating systems. This is very commonly used by regular malware (such as ransomware) as well as targeted malware.
Disabling AutoRun and AutoPlay. Disables AutoRun / AutoPlay for all devices. This prevents applications from automatically executing when you plug a USB stick into your computer.
Disables powershell.exe and powershell_ise.exe execution via Windows Explorer. This prevents the use of PowerShell by malicious code trying to infect the system. You will not be able to open PowerShell directly anymore.
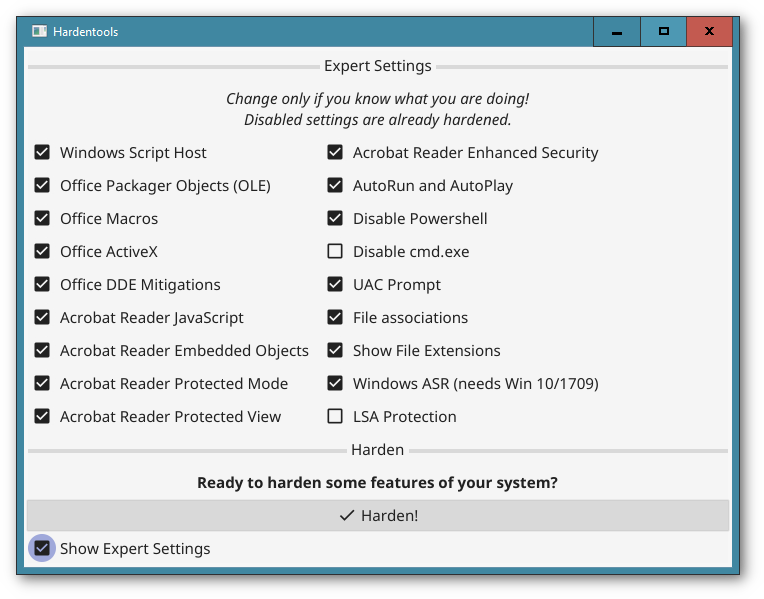
Disables cmd.exe execution via Windows Explorer (optional). You will not be able to use the cmd terminal and it should prevent malicious code trying to infect the system by using cmd.exe to e.g. start powershell.exe. This setting is optional because cmd.exe is used quite often by users and applications. This must therefore be enabled manually in the expert settings section.
Sets User Account Control (UAC) to always ask for permission (even on configuration changes only) and to use "secure desktop".
Disable file extensions mainly used for malicious purposes. Disables the ".hta", ".js", ".JSE", ".WSH", ".WSF", ".scf", ".scr", ".vbs", ".vbe" and ".pif" file extensions for the current user (and for system wide defaults, which is only relevant for newly created users).
Shows file extensions and hidden files in explorer. This is very useful to detect files pretending to be another file type (e.g. an exe file named like iAmSimulatingToBeAPdf.pdf.exe)
Activates additional LSA Protection (Optional / Expert Setting): With this setting enabled Windows provides additional protection for the LSA processes to prevent reading memory from and code injection by non-protected processes. This provides added security against reading of credentials by malicious processes.
Windows Defender Attack Surface Reduction (ASR) rules. Enables various remediations using ASR rules starting with Windows 10 / 1709. To be effective this needs the following prerequisites:
Windows 10 version >= 1709,
You are using Windows Defender Antivirus as the sole antivirus protection app,
Real-time protection is enabled in Windows Defender.
Cloud protection is enabled in Windows Defender (only needed for some of the ASR rules)
The following ASR rules are implemented:
Block executable content from email client and webmail
Block Office applications from creating child processes
Block Office applications from creating executable content & from injecting code into other processes
Block JavaScript or VBScript from launching downloaded executable content
Block execution of potentially obfuscated scripts
Block Win32 API calls from Office macros
Block untrusted and unsigned processes that run from USB
Use advanced protection against ransomware
Block process creations originating from PSExec and WMI commands
Block Office communication application from creating child processes
Block Adobe Reader from creating child processes
Block persistence through WMI event subscription
Block credential stealing from the Windows local security authority subsystem
The following ASR rules are not implemented right now:
Block executable files from running unless they meet a prevalence, age, or trusted list criterion (due to too much impact, e.g. hardentools might get blocked)
Microsoft Office
Disable Macros. Macros are at times used by Microsoft Office users to script and automate certain activities, especially calculations with Microsoft Excel. However, macros are currently a security plague, and they are widely used as a vehicle for compromise. With Hardentools, macros are disabled and the "Enable this Content" notification is disabled too, to prevent users from being tricked.
Disable OLE object execution. Microsoft Office applications are able to embed so called "OLE objects" and execute them, at times also automatically (for example through PowerPoint animations). Windows executables, such as spyware, can also be embedded and executed as an object. This is also a security disaster which we observed used time and time again, particularly in attacks against activists in repressed regions. Hardentools entirely disables this functionality.
Disabling ActiveX. Disables ActiveX Controls for all Office applications. ActiveX controls can provide additional functionality in documents and are mostly used in enterprise environments. The impact of this setting is that ActiveX controls do not initialize and you are not notified that the ActiveX controls are disabled. Note: This doesn't disable ActiveX in Internet Explorer.
Disable DDE and Excel Links. Disables DDE for Word, Excel and Outlook. The DDE protocol allows to send messages between applications to share data. This is an attack vector if the user opens a malicious document. Side effects are:
If there are links to other office documents (to update data in a excel sheet for instance) this data is not updated automatically anymore. If you are using such kinds of documents you might have to disable this harden setting.
Every Excel document is opened in a separate Excel instance if opened using Windows explorer. This might also have impact on sharing data between the documents and consume more memory.
Acrobat Reader
Disable JavaScript in PDF documents. Acrobat Reader allows to execute JavaScript code from within PDF documents. This is widely abused for exploitation and malicious activity.
Disable execution of objects embedded in PDF documents. Acrobat Reader also allows to execute embedded objects by opening them. This would normally raise a security alert, but given that legitimate uses of this are rare and limited, Hardentools disables this.
Switch on the Protected Mode. When protected mode is enabled, Acrobat Reader assumes all PDFs are potentially malicious and confines any processing they invoke to a sandbox so that malicious PDF files can't infect the computer. (This setting is enabled by default in current Acrobat Reader versions.)
Switch on Protected View for all files from untrusted sources. In the Protected View mode, most features are disabled to prevent malicious PDF files to do harm. You can view the PDF, but not do much else. A yellow bar displays on top of the Reader window. Click Enable All Features to exit the Protected View. but do that with caution and only for files you are really sure to originate from a trusted source.
Switch on Enhanced Security. This setting disallows PDF files to fetch data from untrusted locations. (This setting is enabled by default in current Acrobat Reader versions.)
Bear in mind, after running Hardentools you won't be able, for example, to do complex calculations with Microsoft Office Excel or use the Command-line terminal, but those are pretty much the only considerable "downsides" of having a slightly safer Windows environment. Before deciding to use it, make sure you read this document thoroughly and understand that yes, something might break. In case you experience malfunctions as a result of the modifications implemented by this tool, please do let the developers know.
What Hardentools IS NOT
Hardentools is NOT an Antivirus. It does not protect your computer. It doesn't identify, block, or remove any malware.
It does NOT prevent software from being exploited.
It does NOT prevent the abuse of every available risky feature.
It does NOT prevent the changes it implements from being reverted. If malicious code runs on the system and it is able to restore them, the premise of the tool is defeated.
How to use it
Once you double-click on the icon, depending on your Windows privileges, you are asked if you want to run Hardentools with administrative privileges. If you select "No" only a subset of the harden features is available, but you can also use hardentools if you have only restricted privileges to harden your user account. If you select "Yes", depending on your Windows security settings, you should be prompted with an User Access Control dialog asking you confirmation to allow Hardentools to run. Click "Yes".
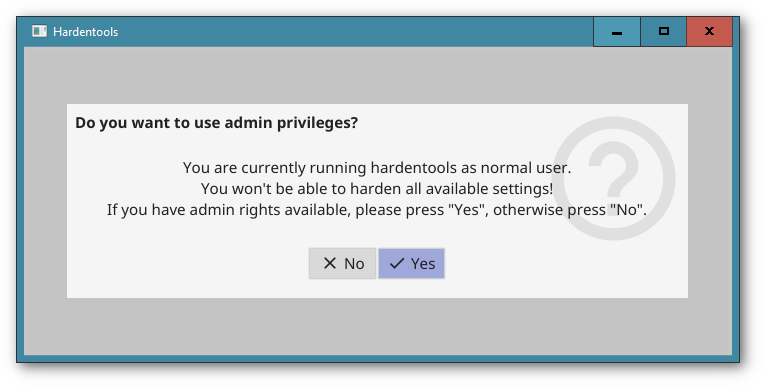
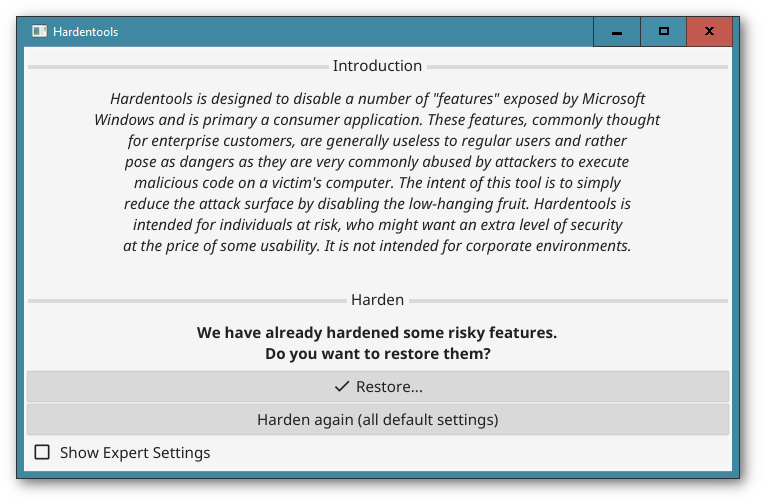
Then, you will see the main Hardentools window. It's very simple, you just click on the "Harden" button, and the tool will make the changes to your Windows configuration to disable a set of features that are risky. Once completed, you will be asked to restart your computer for all the changes to have full effect.
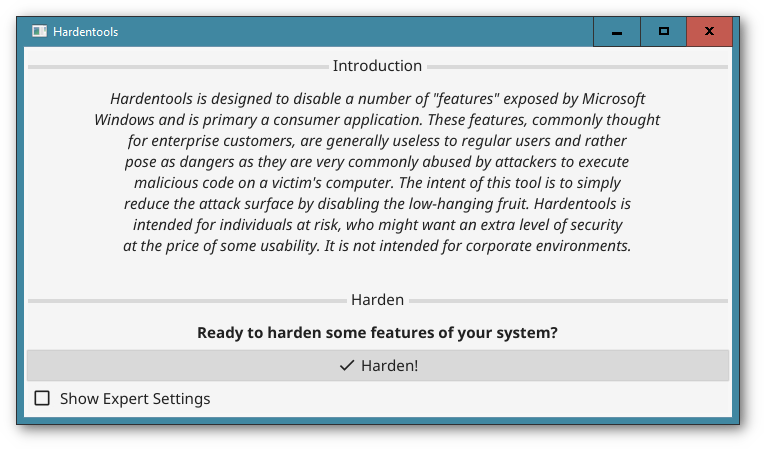
Note: You can select the expert settings checkbox to be able to select or deselect specific harden measures. Please only use this if you know what you are doing.
In case you wish to restore the original settings and revert the changes Hardentools made (for example, if you need to use cmd.exe), you can simply re-run the tool and instead of an "Harden" button you will be prompted with a "Harden again (all default settings)" and a "Restore..." button. Selecting "Restore" will start reverting the modifications. "Harden again" will first restore the original settings and then harden again using the default settings. This comes in handy if you have started a newer version of hardentools and you want to make sure the most current features are applied to your user.
Please note: the modifications made by Hardentools are exclusively contextual to the Windows user account used to run the tool from. In case you want Hardentools to change settings for other Windows users as well, you will have to run it from each one of them logged in.
Known Issues
Hardentools not working in a Virtual Machine or if used with RDP
Hardentools might not start when used on a Virtual Machine or of used via RDP. If started on the command line an error similar to the following appears:
2020/09/06 02:24:47 Fyne error: window creation error
2020/09/06 02:24:47 Cause: APIUnavailable: WGL: The driver does not appear to support OpenGL
2020/09/06 02:24:47 At: /home/travis/gopath/pkg/mod/fyne.io/fyne@v1.3.0/internal/driver/glfw/window.go:1133
This is due to a bug in the UI framework used (https://github.com/fyne-io/fyne/issues/410). You can check if your VM supports an OpenGL 2.0 graphics driver and install that to get it working. We are also working on a command line interface to remediate this.
In cases you get this error, you can use the hardentools-cli.exe to harden the system using the default settings with:
.\hardentools-cli.exe -harden
and restore with:
.\hardentools-cli.exe -restore
Credits:
This tool is developed by Claudio Guarnieri, Mariano Graziano and Florian Probst.
Changes:
v2.1
Sep 04, 2021
Please download and use "hardentools.exe" for normal use cases.
No changes since 2.1-rc1.
Changes since 2.0:
Update of UI Framework (fyne.io 2.0.1)
Additional command line client (hardentools-cli) for special use cases
prevent dynamic dll sideloading attacks for fyne.io dll loads
Fix missing file extensions hardening for unprivileged users
Now also hardens Acrobat Reader 2020 non-DC version
This download is for the graphical Windows version. If you need the command line version, download here.
Click here to visit the author's website.
Continue below for the main download link.
|
















 , out of 56 Votes.
, out of 56 Votes.